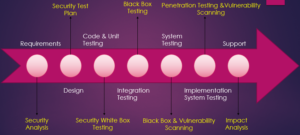
Top 5 Security Testing Types
Security Testing Types
There are many types of security testing, and it’s important to choose the right kind for your needs. These types of tests measure the probability and impact of a given risk. They ensure that a system or application meets predefined requirements and has the appropriate components for securing it. They also provide valuable insight into a business’s risk, and contribute to the evaluation of overall threats. Learn more about these types of tests and how they can benefit your business.
During the assessment, security tests assesses the system for vulnerabilities that attackers may exploit. These vulnerabilities could include unpatched operating systems, weak authentication, or even basic security controls. The purpose of security testing is to determine the risk that an attack could cause and to recommend measures to mitigate that risk. In addition to providing assurance that a vulnerability is fixed, security testing can also be used to identify the effectiveness of the resulting security measures.
Web application penetration testing uses a framework to create a process for evaluating web applications. The guidelines are comprehensive and help testers find common vulnerabilities and complex logic flaws. The updated guide contains 66 guidelines for penetration testing. This framework is an industry standard, and helps organizations curb application vulnerabilities. For a more detailed assessment, organizations should consider incorporating its standards during development. This way, testers will be able to apply a common method throughout the entire organization.
Top 5 Security Testing Types
Another popular security testing tool is Acunetix. This automated vulnerability scanner can audit complex management reports and identify malware in web servers. It also follows the API-First development model, allowing developers to access its features through an API. Users can integrate Probely into a Continuous Integration pipeline. It can detect over 4500 vulnerabilities and help companies determine if their applications are up to par. Acutetix can also help organizations evaluate their network security to meet specific compliance requirements.
Penetration tests, also known as pen tests, are a more intrusive method. Unlike vulnerability scans, penetration tests can corrupt machines, cause denial of service, and reduce productivity. Red team exercises, on the other hand, often involve a team of hackers who attempt to breach a system without the knowledge of employees. For such a test, management and blue team leads must be informed. This will help ensure that the appropriate response is made.
Vulnerability research is an important part of security testing, as it helps organizations meet compliance standards. CERT Coordination Center, Google, and HackerOne are all partners with this security testing company. The company has found over 120,000 vulnerabilities in the past two years and has paid out over $80 million in bug bounties to hackers. Similarly, a network analysis tool called Nmap is an important piece of security testing software. The software is capable of detecting open ports, services running on them, and operating systems.
Web application penetration testing is a more sophisticated type of security testing. It focuses on web applications and browsers, and identifies vulnerabilities and recommends countermeasures to mitigate those risks. Web application penetration testing is considered more difficult and comprehensive than traditional security tests, and it requires a lot of planning and time to perform successfully. You can hire a certified security tester to conduct a web application penetration test for you. You can also hire a company to perform a web application penetration test, but it’s important to choose the right type for your needs.